Accessing Azure File Shares can sometimes result in errors, especially when using the mount script copied from the Azure Portal. A common issue is the “Access Denied” error, which may occur when configuring Azure Files as part of an Azure Virtual Desktop (AVD) environment. This guide explores the root cause of the issue and provides a resolution, comparing the Net Use command method with the Azure Portal script approach.
Key Use Case
This troubleshooting scenario typically arises in environments where:
- FSLogix Profile Containers are used with Azure Files.
- The Azure Storage Account is joined to on-premises Active Directory (AD).
- Group Policy Objects (GPOs) restrict credential storage, causing authentication failures.
Problem Overview
When attempting to mount Azure File Shares using the script provided by the Azure Portal, users may encounter an “Access Denied” error. This issue persists even when:
- Using a new AVD host.
- Testing with different user accounts.
Observations
- Error in Logs
- The backend logs (collected via DGrep and Log Collector) show an Access Denied error.
- The error includes “KerberosClientOtherError”, which indicates that Kerberos authentication is being used instead of the Storage Account Key credential.
- Working vs Non-Working Methods
- Net Use Command: Successfully mounts the Azure File Share using the Storage Account Key.
- Azure Portal Script: Fails due to Kerberos authentication being used instead of the provided Storage Account Key.
Root Cause
The issue is caused by the following factors:
- Credential Manager Behavior
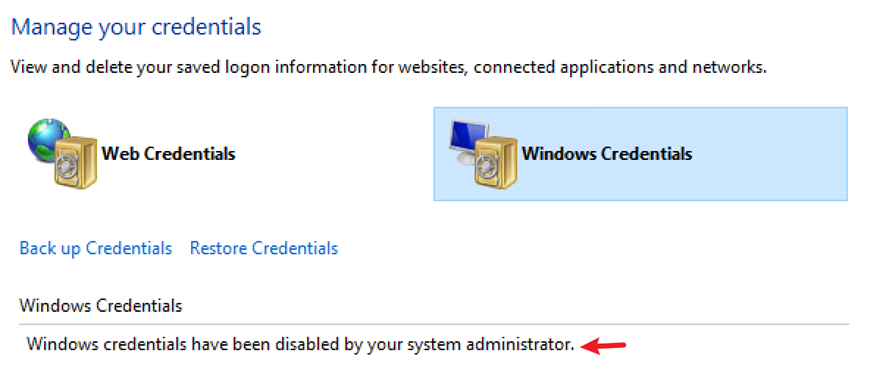
- The Azure Portal script saves the Storage Account credentials to the Windows Credential Manager.
- If the credentials cannot be cached (due to GPO restrictions or cache failures), the script defaults to using the current user’s credentials for authentication.
- Group Policy Restriction
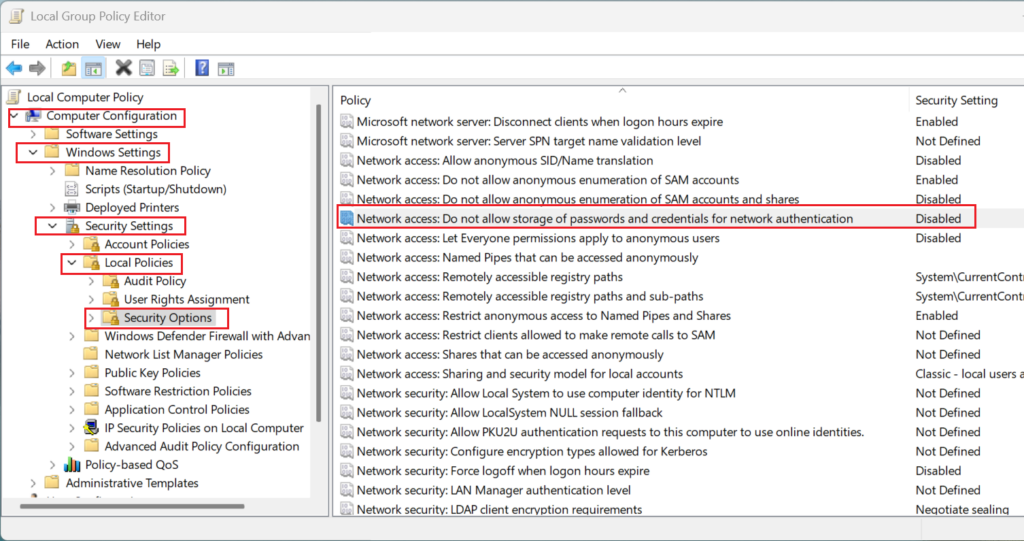
- The GPO setting “Network access: Do not allow storage of passwords and credentials for network authentication” prevents the Credential Manager from storing credentials.
- As a result, Kerberos authentication is attempted, which fails due to insufficient NTFS permissions.
Troubleshooting Steps
Step 1: Verify the Error
Perform network trace analysis for both methods:
- Net Use Command: Establishes SMB connection successfully using the Storage Account Key.
- Azure Portal Script: Attempts Kerberos authentication, resulting in an Access Denied error.
Step 2: Test with Net Use Command
The following Net Use command bypasses Credential Manager and directly provides the Storage Account Key for authentication:
net use <desired-drive-letter>: \\<storage-account-name>.file.core.windows.net\<share-name> <storage-account-key> /user:Azure\<storage-account-name>
Why This Works:
- The credentials are explicitly provided in the command.
- No dependency on Credential Manager or Kerberos authentication.
Step 3: Analyze Group Policy Settings
Run the following command to check the Group Policy configuration:
gpresult /h c:\temp\computer.html
Inspect the resulting HTML file for the GPO setting:
“Network access: Do not allow storage of passwords and credentials for network authentication”
If this setting is enabled, the Azure Portal script cannot save credentials in the Credential Manager, causing authentication failures.
Step 4: Resolution
Disable the Restrictive GPO
- Open Group Policy Management on the domain controller.
- Locate the policy:
Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options
- Network access: Do not allow storage of passwords and credentials for network authentication.
- Set the policy to Disabled.
Once this policy is disabled, the Azure Portal script can store credentials in the Credential Manager, allowing successful authentication.
Comparison: Net Use Command vs Azure Portal Script
| Method | Authentication Mechanism | Dependency | Outcome |
|---|---|---|---|
| Net Use Command | Storage Account Key | No Credential Manager | Successful |
| Azure Portal Script | Kerberos (fallback if cache fails) | Credential Manager | Fails if GPO restricts cache |
Additional Tips
- Testing in Lab Environments
Simulate the issue by enabling the GPO setting:
Network access: Do not allow storage of passwords and credentials for network authentication. - Documentation Reference
Follow the official guide: Set up FSLogix Profile Container with Azure Files and AD DS or Microsoft Entra Domain Services. - Network Configuration
Ensure port 445 is open for SMB traffic. If blocked, use Azure VPN or ExpressRoute to tunnel SMB traffic.
Conclusion
The Access Denied error when using the Azure Portal script to mount Azure File Shares is often caused by restrictive GPO settings that prevent credential caching. Using the Net Use command provides a reliable workaround by bypassing Credential Manager and directly supplying the Storage Account Key. Disabling the restrictive GPO resolves the issue for the Azure Portal script method.